What Works in Active Threat Incidents: Best Practices for the K-12 Environment
Updated July 25, 2019
As a school security professional for more than 30 years, I have responded to many kinds of emergencies and situations. School districts face safety and security challenges that are multifaceted and complex and must be prepared to address a full range of situations that pose risks to students and staff, including everyday occurrences like weather emergencies; however, the most serious and life-changing events I have responded to include “active threats,” including an active shooter attack on one of our high schools, suicides with firearms on campus and many threats of violence towards the schools. An active threat is any situation that presents an immediate danger to school occupants. In addition to individuals using firearms, other types of weapons and behaviors could also create active threat situations.
When it comes to preventing school violence, districts must strike an effective balance between physical security measures and human behavioral prevention approaches. In February 2019 a study was released on averted and completed incidents recorded in the U.S. Department of Justice Averted School Violence (ASV) database, which makes clear that different types of attacks pose different prevention challenges. According to the study, schools “have the chance to pick up on warning signs and intervene” with insiders like current or recent students or employees, but when the attacker is “someone with no connection to the school, the school usually has no way of anticipating the attack.” In the event other prevention efforts fail, facility security measures are critical to protection, mitigation and response.
Here are my observations on what worked well as well as some of the shortcomings that became evident during active threat incidents. The best practice recommendations below align with the PASS Safety and Security Guidelines for K-12 Schools, and I encourage you to check out this PASS resource for additional information and to learn more.
The Place to Start
Staff responsible for school safety and security need district leadership at the superintendent and board levels to build holistic safety programs. Coordination with executive management at the district level is integral to the successful development and adoption of school safety processes, plans, technologies and procedures and for ensuring these measures are updated for consistency with evolving best practices. Most school safety measures have district-wide components and responsibilities. It is critical for district leadership to understand the fundamental link between readiness for day-to-day emergencies and disaster preparedness. School districts that are well prepared for individual emergencies involving students or staff members are more likely to be prepared for complex events like a community disaster or an active shooter incident.
Create a Safety Team
Security planning teams should include key stakeholders in the K-12 environment. The process of forming a team should be led by an experienced security director, if a district is fortunate enough to have full-time staff in this position, or a staff member who has security as a primary responsibility. Start with a basic team including:
- Security director (or person in charge of security)
- School administrators (across functions such as operations, mental health,secretarial and human resources)
- Security/systems integrator and/or consultant
- IT director
- Local police and fire officials
This team must be given the flexibility to form the district’s safety processes, plans, technologies and procedures. Having a team that represents a broad range of responsibilities and expertise helps to address all the potential hazards a school district may face. Each safety team member should understand the layered approach to security outlined in the PASS Guidelines and recognized in other school security resources.
Layers of Protection
District-Wide Layer
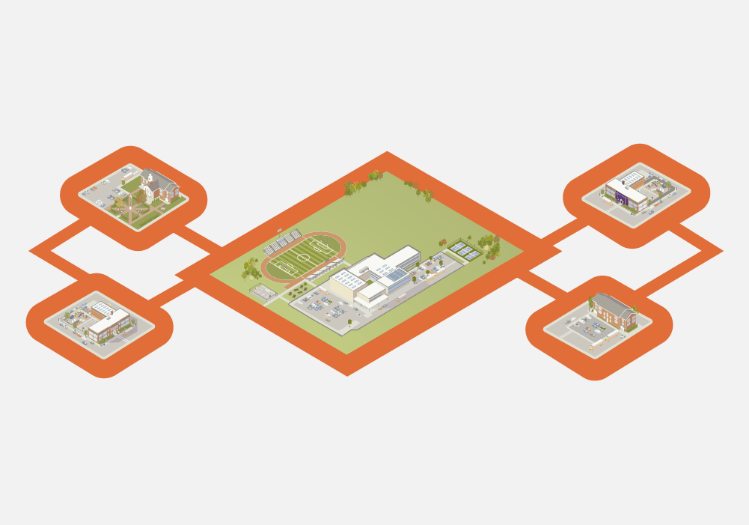
Leadership and coordination at the district level are integral to the successful development and adoption of school safety processes, plans, technologies and procedures and for ensuring these measures are updated for consistency with evolving best practices. Most school safety measures have district-wide components or responsibilities.
Property Perimeter Layer
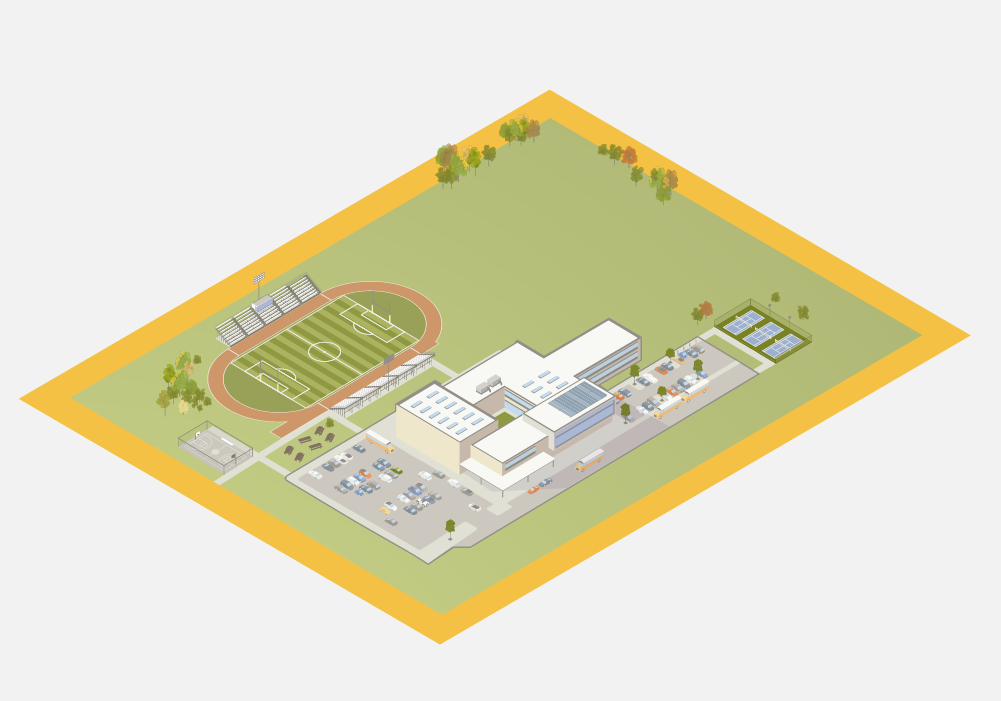
The property perimeter layer begins at the school property boundary and extends to the parking lot. This area includes playgrounds, sporting fields and other facilities that are often used by the public after school business hours end. The physical security of a school facility begins at the property perimeter, where the most outwardly visible security deterrents to an external threat can be implemented.
Parking Lot Perimeter Layer
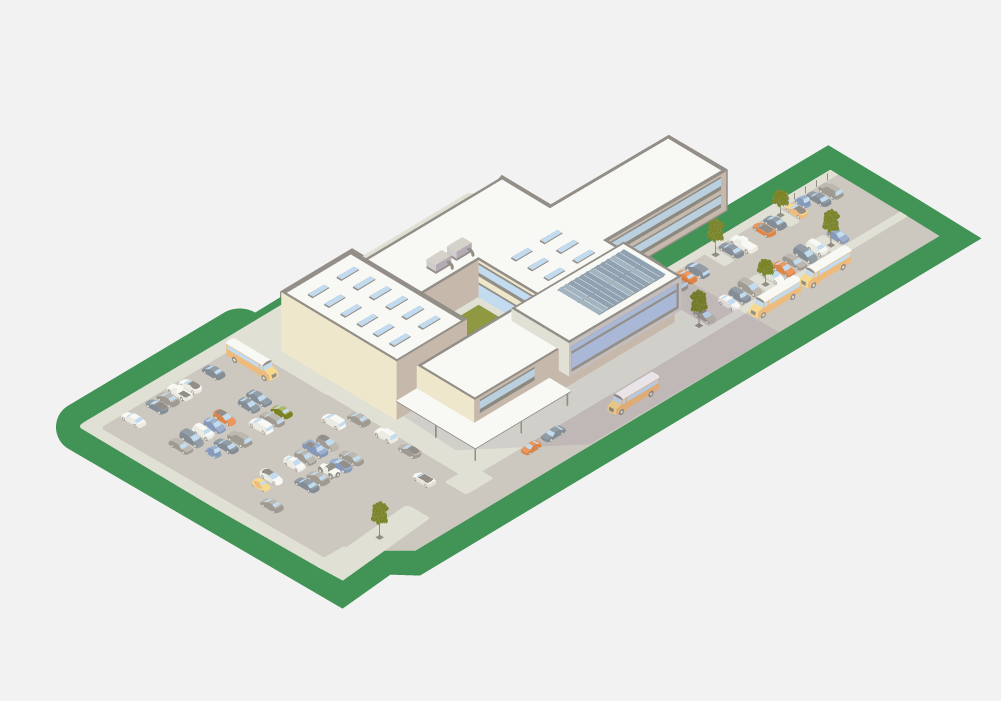
Within the parking lot perimeter, staff, students and visitors park their vehicles or arrive and depart by bus or other means. Just like the property perimeter layer, the parking lot perimeter should always be clearly defined. In many cases, this area is where schools experience the most safety issues.
Building Perimeter Layer
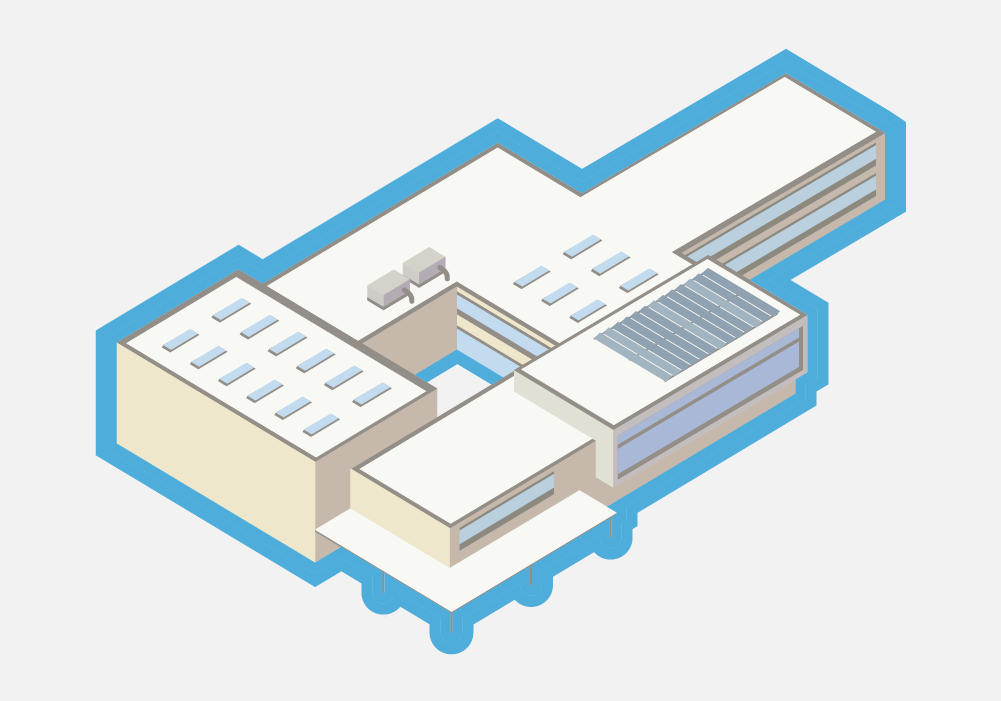
The building perimeter layer begins with school grounds adjacent to the exterior structure of a building and consists of the perimeter of a building itself, including the exterior doors and windows of a school. Securing a building perimeter can range from simple to complex, especially for middle schools or high schools with multiple buildings/open campuses. Key safety and security functions take place within this layer, as it encompasses all areas where people enter and exit a school building.
Classroom/Interior Perimeter Layer

The classroom/interior perimeter layer consists of a school’s entire interior, including not only classrooms but also gymnasiums, cafeterias, media centers, etc. This is both the last layer of defense against external threats and, often, the first protection against internal threats to student, staff and visitor safety.
Understand the Risk at Your Schools
A risk assessment is the first step toward developing a comprehensive security plan and thus a prerequisite for decisions regarding deployment of security solutions to address the potential for active threats. Several options for conducting risks assessments are available through:
- Local police and fire officials (ability varies by jurisdiction)
- U.S. Department of Homeland Security Protective Security Advisers
- Independent consultants
- Security design consultants/systems integrators
- Internal assessment using free assessment tools
- Assessment by local subject matter experts assembled by districts
Regardless of what method is chosen, it’s important to understand that risk assessment and mitigation can never eliminate risk; however, risks can be identified, measured and reduced.
Create Threat Assessment Processes and Procedures
Over the years, it has become quite clear that school districts must find an effective balance between deploying security technologies and human behavioral prevention approaches. Most school districts financially struggle to find this balance. For many years, our security team has worked very closely with our district’s mental health professionals. After the attack on Arapahoe High School in my district in 2013, this endeavor became even more robust because it was realized that we had to try to get ahead of school violence by looking for the signs and even being more proactive in our interventions. It is obvious by looking at these events that the perpetrators before these events often express disturbing signs and behaviors. Just like we do building security assessments, it sometimes becomes necessary for a school district to assess people as potential threats, commonly referred to in school safety as a threat assessment. School districts should develop and implement threat assessment procedures which must be clearly implemented and communicated to students, families and staff. Obviously a threat assessment is intended to prevent violence and involves both assessment and intervention. Threat assessment involves determining whether a student poses a threat of violence. This will also include determining if the student has the means to act. Most students who pose a threat indicate their intentions in some way. Examples can include writings, thoughts spoken to others and drawings and posts on social media that threaten harm. Threat assessment recommendations from the National Association of School Psychologists can be accessed at nasponline.org.
What Has Worked During Active Threat Incidents
Essential Policies and Procedures
Equipping and empowering staff and students to make response decisions is the single most important factor in mitigating active threats. During an active shooter attack on one of the schools in my district, we observed that immediate actions by staff and students had a direct limiting/mitigating impact on the ability of the perpetrator to cause further harm after an initial attack.
Both staff and students should receive age-appropriate training and drills that emphasize survival skills and decision options. In my district, our core active threat protocol consists of four situation-dependent options: SHELTER-EVADE-DEFEND-CARE.
- SHELTER: Alert others. Any staff member should be able to initiate a lockdown when they detect a threat. Call 911 when safe to do so. Lock the door(s) and shut off the lights. Get students, staff and visitors quiet in a low position behind large items that might provide extra protection out of corridor line of sight, and ready to move if necessary. Account for those in your care. Do not open the doors for anyone – responders will come to you. If in a corridor, shelter in the nearest safe room. If the fire alarm goes off (during an active threat situation) stay where you are unless threatened by smoke and fire. Be prepared to EVADE-DEFEND-CARE.
- EVADE: If not able to get to a safe location in the building, identify and run away from commotion. Find the nearest exit and flee to a safe location. In a classroom consider your door and window escape options if the threat approaches. If a threat is nearby and you cannot seek cover safely, seek concealment (hide). If outside, flee away from the threat in the opposite direction to the nearest safe cover. Call 911 when safe. Be prepared to SHELTER-DEFEND-CARE.
- DEFEND: As a last resort and only if your life is in imminent danger, attempt to incapacitate a threatening person by any means possible. Be prepared to EVADE-SHELTER-CARE.
- CARE: Call 911. Be a leader. Reassure and provide comfort to those around you or in your care. Give emergency first aid to the best of your abilities to those who are injured. Be prepared to EVADE-SHELTER-DEFEND.
Supporting this active threat protocol are standard emergency procedures that every employee should be trained to independently initiate during both active threats and other scenarios as needed:
- Lockdown: A lockdown usually involves locking and closing doors, moving students out of sight and requiring students to remain quiet within the room. Lockdowns should continue to be included in any an options-based approach to active assailant training, which provide students and staff with a range of alternative strategies to save lives and the permission to use them, considering variables such as the nature of the threat, time of day and location of students. Like other safety drills (e.g., fire or tornado), it is important that the ages and developmental levels of students and the physical layout of the school campus (e.g., ease of access to outside doors and proximity of places to hide other than classrooms) are considered when communicating to students and staff concerning lockdown.
- Secured Perimeter (Lockout). A secured perimeter addresses threats outside the building, often initiated when there are emergency situations taking place in neighborhoods nearby, such as a crime in progress, police activity or a dangerous animal in the area.
- Shelter in Place. Shelter in place is initiated in situations that may require staff and students to shelter in their classrooms or work areas; it is more restrictive than a secured perimeter, as staff and students are not allowed to move within the building. Unlike in a lockdown, however, staff and students can remain at desks or work spaces. Shelter in place is generally initiated when there is a possibility that an area emergency may escalate and having students and staff sheltered behind locked doors may be critical to safety and order.
- Evacuation. The purpose of an evacuation is to quickly get students and staff out of the building by a route designed to avoid contact with a potential threat, which could include: a known threat inside the building, such as a suspicious package, a threatening person in a specific confined area or a hazardous material spill.
- Reverse Evacuation. A reverse evacuation procedure is used to get students and staff into the safety of a building to avoid contact with a potential threat when the location of the threat outside the building is known.
- Room Clear. A room clear procedure is initiated by a teacher or supervising adult to send students away from a potential threat, such as a student acting out in a violent manner; it is also used when the teacher must remain in the dangerous situation but can send students to a designated safe area.
Proven emergency response planning, methods and training should be established at the district level to ensure the most effective responses when procedures are activated. School districts should formally adopt through board policy the National Response Framework (NRF) and National Incident Management System (NIMS) developed by the Federal Emergency Management Agency. When adopting NRF and NIMS, a school district should implement an incident command system (ICS) within the entire organization as the coordinating link between multiple agencies and jurisdictions in an emergency response.
In my district for example, we have established teams of professionals in the following roles to address active threat incidents (and other incidents) as well as the aftermath.
- District crisis response team (ICS)
- Building crisis response team (ICS)
- District safety planning team
- Building safety planning team
- Multi-agency crisis planning team (can be combined with the district safety planning team)
- Threat assessment team
- Psychological recovery team
In an active shooter incident it is also important to note that all of the schools in a community are going to be impacted in the event – not just the school that is being attacked. School safety leaders at nearby schools must carefully implement emergency protocols during the event as well. In the initial minutes of an attack nearby, school safety leaders must consider the possibility that the initial incident could also be the start of a coordinated attack on other facilities. For example, in Colorado during the STEM active shooter incident in May 2019, neighboring districts took into account that several of their schools were within a short distance, just over a mile away. When the attack began, neighboring districts placed all of their schools into a shelter in place status in order to ensure staff and students would be ready if the attacker moved into a nearby area. The same protocol had been followed in December 2013 when Arapahoe High School was attacked. During these incidents, it is important to note that many of the community’s emergency resources are going to be pooled at the scene of the attack. Ensuring staff and students are secured in safe places during such incidents is important.
It is very important for each school to have a good reunification plan in place. In my district, we have three types of reunification plans that include: a bus reunification, classroom reunification and a large group area reunification. During the Arapahoe incident, there was a large group reunification for the high school at a nearby church. Additionally, there were classroom reunifications for all the other schools as all of the community’s resources such as police, fire and transportation were engaged with the response at Arapahoe. Reunifying the students with their guardians insured their safety and that they would not be released into a community where the normal safety measures were disrupted.
It is also suggested that every school district and community remember to establish policies and procedures for other hazards that could impact the schools. Many of these potential hazards are far more likely to happen than an active shooter incident.Each district should ensure that, within the policies and procedures established for staff and students, parents, volunteers and any others that interact with the school community, the following are covered:
- School safety/NIMS compliance
- All-hazards procedures
- Staff safety training
- Threat assessment
- Discipline
- Harassment and bullying
- Use of technology
- School engagement and truancy
- Pandemic procedures
- Food allergies and handling procedures
- Mail handling procedures
- Drug and alcohol prevention
- Student safety training
- Staff assignments for supervision of students within layers (see below)
- Violence prevention, awareness and reporting procedures
- Suicide prevention, response and reporting
- Mental health issues (e.g., depression)
- Child abuse
- Violence prevention, awareness and reporting procedures
- Plans and procedures for students, staff and community members with disabilities
Facility and Vicinity Mapping
In all the large incidents, there is always a need for responders to have facility and vicinity mapping. In fact, after the 1999 Columbine shooting, my district assisted with ideas on how bring this information electronically out in the field. A program was created called the School Emergency Management Planning Software (SEMPS), which my district still uses a version of to this day. SEMPS provides a virtual tour of the entire facility and contains comprehensive, interactive, hyperlinked information that includes emergency contacts, main utility shutoff locations, building floor plans, maps, video photography, related community information and aerial photographs. Programs like SEMPS don’t cost anything to implement except time..
PASS recommends the following:
- Districts should ensure that each facility can provide an overall floor plan, a roof plan, fire, HVAC, security systems and other emergency information useful to police, fire and other emergency partners.
- Printed or electronic copy of “As-Built/Record Drawing” of the subject facility. Plans should include all room names and associated numbers (see discussion of door and window numbering systems under the building perimeter layer).
- Printed or electronic copy of an aerial view of the subject facility. This should include a minimum five-block radius outside the school property perimeter.
It is further recommended to keep paper and digital copies stored on digital media or other devices.
Key Technologies
Mechanical Door Locks
Although hard-wired electronic access control systems offer the most secure solutions, they may not always be the most viable option for all openings due to budget constraints. Securing doors with a key-controlled master key system is one of the most cost-effective means of securing a facility. There should also be a documented key control policy in place. During active threat incidents, the ability to a lock a door must be given to staff and students (e.g., physical locks that can be engaged by a push button or lever from the inside of the classroom). While some stakeholders may have concerns with giving students the ability to lock a door, active threat incidents could come at any time, including when a teacher is not in a classroom or when students may need to use an unoccupied room for shelter. Students of all ages should be empowered and trained on how and when to lock a classroom door.
It is also a good practice for a school district to have mechanical door lock and key control policies and procedures consistent with the following:
- Classifying entrances as either primary, secondary or tertiary
- Securing entrances into the school by blanking out (or deactivating) keyed locks of doors that are not necessary for ingress (secondary or tertiary)
- If an access control system is in place, placing key locks on these doors for a backup (primary)
- Maintaining an exterior master key system (preferably removable core type) separate from the interior door system (In the event a key is lost, only exterior doors need to be rekeyed in order to secure the building. Using removable cores facilitates a quick and less expensive method of rekeying.)
- Establishing an exterior master key for an entire district or for each individual building
- Ensuring that all classrooms, gymnasiums, cafeterias, media centers, etc., have full access by all staff to allow access through locked doors in an emergency situation
- Keeping several sets of master keys available to be handed out to tactical units during an incident
Stand-Alone and Wireless Access Control Locks
One of the most exciting security industry innovations is that lock manufacturers are now making older mechanical locks compatible with electronic solutions such as standalone and wireless access control locks. Many schools across the country have interconnected classrooms, partitions and large spaces with multiple entrances that would be quite the challenge for staff students to secure during an attack. Most districts experience these challenges. One of the biggest fears for teachers that have interconnected classrooms is, what if the adjacent classroom did not lock the door? These technologies help insure all the doors get locked. When putting these technologies in place, the end user should consider these points:
- Locks should have a visual indicator. From the interior of the room, the condition of the lock (locked or unlocked) is visible to room occupants.
- Staff in these classrooms should be provided with wireless fobs that lock the door.
- If the school has lockdown and mass notification system, these fobs should be tied into the system to initiate the lockdown and lock the doors
- There are multiple wireless systems on the market today. You should research and request demonstrations in search for a system that interfaces/unifies with your existing unified security system.
Radio Communications
Radio communications technology is an essential element of a school’s emergency preparedness needs. Localized radios allow constant communications about what is happening on school grounds. In fact, radios are even utilized more than phones because of how often the employees and students are on the go. The most frequent emergencies that many districts face are related to the weather. Many school districts are starting to utilize the 800mhz radio systems that police and fire officials use. 800mhz systems are also known as “trunked” radio systems. A trunked radio system allows organization of users into different groups and provides the capability to communicate on frequencies used by police, fire, emergency medical services and other first responders in the community, whereas traditional two-way radio systems may be confined to a certain band (frequency) exclusive to the system. Any school district that does not have the capability to have radio interoperability with law enforcement and fire to explore the possibility. Trunked radio systems are the most reliable communication tool, as cellular networks can and do become easily overwhelmed during emergencies.
Video Management Systems
Video surveillance can be used to address risks within the classroom, interior and exterior perimeters by providing surveillance, assessment, forensics and risk mitigation. Having a visual record of student, staff, faculty and visitor activity throughout the day provides another layer of deterrence for unwanted activities. Often, people who plan to commit horrific acts perform site surveillance and probing before an act. Detecting this activity and acting upon it can thwart a hostile act before it begins. A vide management system (VMS) also provides valuable situational awareness during emergencies. Having designated personnel who understand and are trained to use the camera feeds in an emergency is critical. At minimum, these staff should be equipped to use radio systems to communicate to other responders on what is being observed in real time.
School District Security Operations Center
Particularly in large districts, a school can be compared to a city, and when you have multiple schools it is like working with multiple cities. Each school has its own community and culture with potentially hundreds of staff and thousands of students on the campuses. Just like in cities, there are emergencies every day, around the clock. Having a district security operations center can help manage respond to these emergencies in the most coordinated manner and provide situational real-time information to responders.
Access Control Systems
Access control systems are no longer just concerned with card access. These systems are the backbone of a school or district’s entire physical security system. Effective and efficient access control will unify other safety and security technologies (video, alarms and fire) so that they can be utilized in many different productive ways. A unified security system is a force multiplier which empowers personnel district-wide to have a hand in helping keep the schools safe.
Visitor Management Systems
Visitor management systems streamline the visitor sign-in process and track specific visitor data such as who is entering the school and when, the reason for the visit, and who was visited. Additionally, many systems record photos of the visitors or scan driver’s licenses that are presented by visitors. This not only helps confirm the identity of the presenter, but also checks for persons that should not be permitted to enter for a variety of reasons, such as restraining orders or parental rights disputes. Some systems check driver’s license data against the National Sex Offender Database or even run full criminal background checks. Some of the most threatening situations schools face involve potentially hostile visitors such as disgruntled parents and guests.
Video Intercom Buzz-In System
A video intercom should always be used when there is no direct line of sight to the person that is screening incoming visitors. These devices enable schools to speak with and observe visitors at main entrances and any other areas, such as loading docks, where people other than students, faculty and staff need to enter the building. The use of networked video intercoms is recommended, enabling screening from multiple devices such as a monitor in the front office or on mobile devices if needed. Networked video intercoms can also be recorded on the VMS, providing a visual record of activities at entrance points. The intercom should be integrated with an electronic access control system to enable screeners to unlock the door remotely, regardless of the monitoring device they are using.
Motion Detectors, Door Contacts and Beam Detectors
Time-tested intrusion detection technologies that protect school facilities from burglary and theft are also very valuable in active threat situations. Additionally, monitoring the status of the locks is important to ensure the door are not only closed, but the lock is engaged. Motion detectors can be used in search and rescue efforts during an incident.
Duress
Most intrusion detection systems provide the ability to add new devices to the system in a cost-effective manner. One use of the intrusion system is to allow for duress/panic buttons or devices to be installed that provide users with the ability to trigger alarms for a variety of life safety threats. Such devices should be installed in the main office and other public areas that would immediately communicate – and differentiate between – different types of emergencies or threats. Ensuring audio and video feeds in these areas should also be considered.
Remote and Mobile Lockdown Capability
Districts should strive to provide staff in each facility with the ability to lockdown both internally and externally, initiate mass notification and alert responders to emergencies. This can include wearable pendants or other technologies that make it possible to initiate these communications both inside and outside of a school.
Mass Notification
Communication systems should be integrated with the district-wide mass notification system. Within this integration, the school can receive instant alerts for weather and other emergencies that can affect the school. There are a variety of technologies to interface the in-building communication systems to wide-area systems. When using a mass notification system, it is important to include its deployment in your school’s drills.
Special Note on Fire Alarms
It is very possible that during an active threat incident a fire alarm will be initiated from gun smoke, fire or just a panicked person pulling a fire alarm. It is important for a school district to work with their local fire department to work out a solution to over-ride a fire alarm in an active shooter incident. Staff and students must also be taught that in an active threat incident that the rules are active Treat response first and fire drills second.
Prevention, Preparation and Recovery
Empower the Community to Share Concerns Through Anonymous Reporting
One of most effective implementations in school safety is the use of communication tools allowing students and others in the community to anonymously report potential threats and other concerns. This practice has demonstrated success in preventing potential violence. Students often know long before adults do what is occurring in their schools and communities, including fighting and bullying, substance abuse, dangerous and concerning behaviors, threats, depression, suicidal statements and self-injury, witnessed either in-person or online. Some states like Colorado mandate that public schools implement tip line programs. Tip reporting processes should be simple; providing students, parents and community members with a safe way to report information about any issues that concern their safety or the safety of others. It should also meet the following criteria:
- The anonymity of every report should be guaranteed—no caller ID or data tracking.
- The program should be available to all members of the community.
- Calls should be answered immediately, and service should be available 24 hours a day, every day of the week.
- Every tip should be investigated.
In Colorado, this tool is mandatory in all public schools. The State of Colorado provides a program called Safe2Tell. In a single K-12 district, the Safe2tell program generated 500 tips. Lives have been saved and violence averted through the use of the system. Most K-12 security teams will not have systems provided by the government to use; however, there are organizations out there that provide similar services to school districts.
Crisis Management Considerations
It is most important to note that a school district and community will be overwhelmed, distraught, blaming, fearful and just upset in the aftermath of a school shooting. These are some things that have proved helpful for our schools and community in the aftermath in crisis intervention.
- Effective intervention and support around school shootings need to be local endeavors. The best way to support community members’ needs is to work through the school, local providers and agencies. It is important for the district to develop relationships/mutual agreements with other stakeholders before an incident takes place.
- Note that each school and community have their own culture. Crisis management providers must understand this culture before they start working with the community.
- Try to get to new normal as soon as possible. It is paramount to get the school culture back to prior routines as quickly as possible.
- It is common for students, families and school staff to be offered special opportunities in the aftermath as a show of support. This may unintentionally keep the traumatic experience at the forefront of victims’ minds. These special opportunities should be thought out and promote healing. There are people and groups who will try to use these people for financial and political gains. When this happens, it can be quite damaging to the healing process.
- Staff should be trained to provide and or direct seekers to the appropriate immediate, intermediate and long-term programs and interventions that can provide support.
- Experts can provide ongoing consultation and assist local agencies in providing interventions. Local leadership should be encouraged to take a deliberate and thoughtful approach to managing the situation.
Mental Preparation/Resiliency
Active threat situations are highly stressful to those involved in many ways. Responders who are responsible for district safety must be trained and ready to work through the shock and the pressure of the moment. One area of preparedness often overlooked is the effects of live viewing/monitoring of these incidents via modern technology. This can be traumatic for security operators and other staff who are seeing live images of an incident and trying to coordinate a response to an active threat that may be miles away. Districts must also be cognizant that their employees are going to be impacted. Fire and police departments have mental health professionals dedicated to the staff on hand – often, schools do not. Employees must be empowered to understand the symptoms of post-traumatic stress disorder and understand how to seek help if it arises.
Potential Cell Phone Problems in a School Shooting
In the Arapahoe incident, the use of cell phones and mobile data devices was quite challenging. In that incident, almost all emergency communications took place on the trunked radio system because communication on cell phones was impossible. During the recent STEM shooting, upon checking on the schools in my district, I noted the closer proximity to that area of shootings, that cell phone service was impacted to the point where it was useless. The main reason for this is that during these incidents, the natural response of victims is to contact worried family members, who then try to call the victims. With currently deployed wireless networks, there is no solution to this problem. The upcoming 5G networks will hopefully help in these types emergencies. End users should take extreme caution when considering counting on cell phones and cellular data in active shooter incidents, or evaluating emergency communications products that depend on cell phone use.
Victims should focus on staying alive and not a device distracting them from doing so. In active shooter training, staff and students should be made aware that talking on a cell phone and/or the ringing of a cell phone could alert the assailant(s) to their presence.
Segregate Physical Security Networks From Administrative and Student Networks
Security and emergency communications systems (e.g., access control, video surveillance, alarms) should be operating on dedicated physical security networks (subnets and/or VLANs), separate from the districts’ primary operational networks and any student networks, with proper security controls in place. This not only provides better cyber protection for physical security systems, but it also preserves operation of these critical systems if operational networks fail for any other reason. In the Arapahoe incident, during the initial minutes, we lost access to the camera feeds because our systems were not segregated.
Aftermath
Now comes the investigation of the incident. This can be a difficult time since the incident now reverts to a crime scene investigation. Due to the investigation it may be days or months until cleanup and building recovery efforts can begin. This can also be a traumatic time because the crime scenes can be quite disturbing for safety and security staff. In the days, weeks, months and years after a violent event, district and even individual responders will face tremendous scrutiny. Any negative media, hostility expressed by the community and attacks on social media can cause distractions and stress. It is important that team members support each other through these processes from beginning to end.
Conclusion
Violence, injury and loss of life in our schools are a tragedy. Thankfully, most school emergencies are more routine. That is why it is imperative that districts implement solutions that can help address a broad range multiple hazards that could face staff, students and visitors on any given day. Again, check out the PASS Safety and Security Guidelines for K-12 Schools for additional information on best practices for addressing active threats.
Download the PDF version of this article.

Ready to get the Guidelines?
The most comprehensive information available on best practices specifically for securing school facilities, vetted extensively by experts across the education, public safety and industry sectors.
